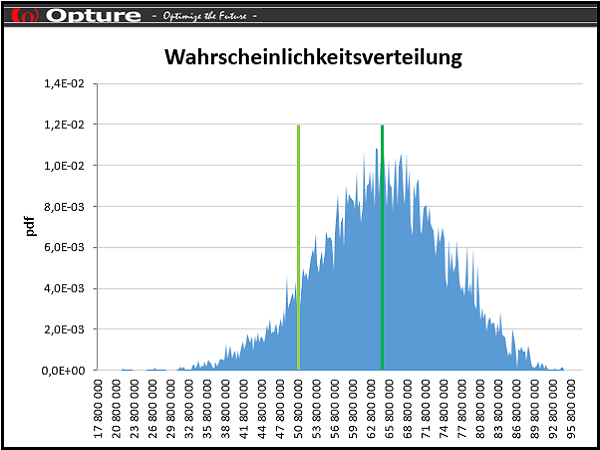
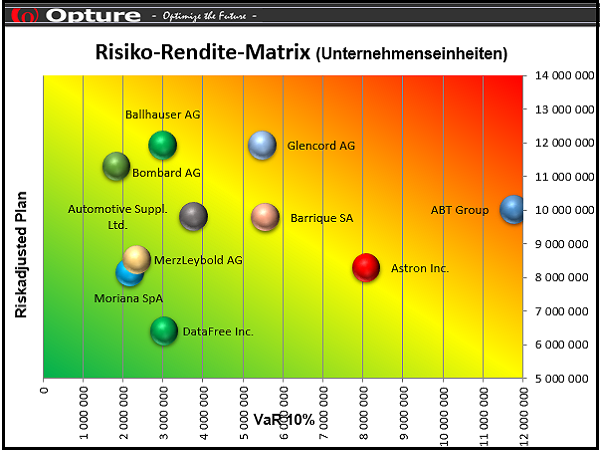
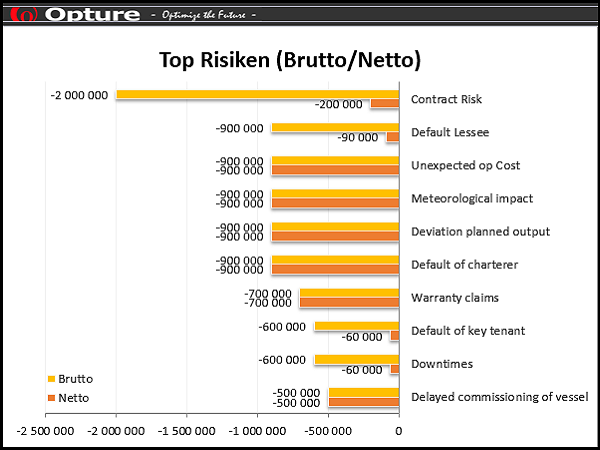
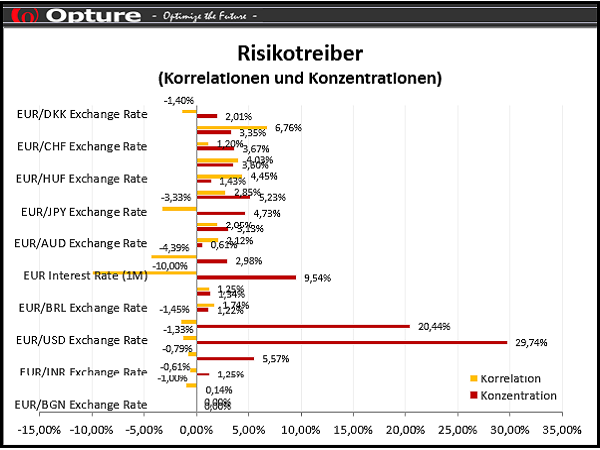
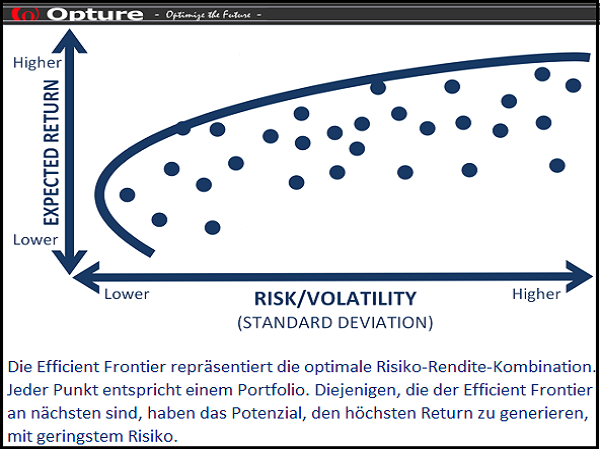
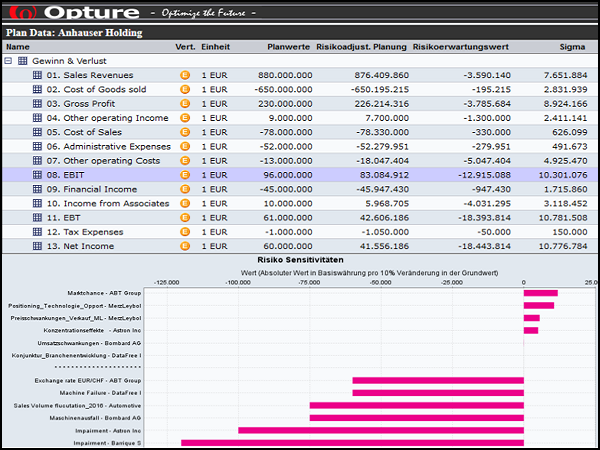
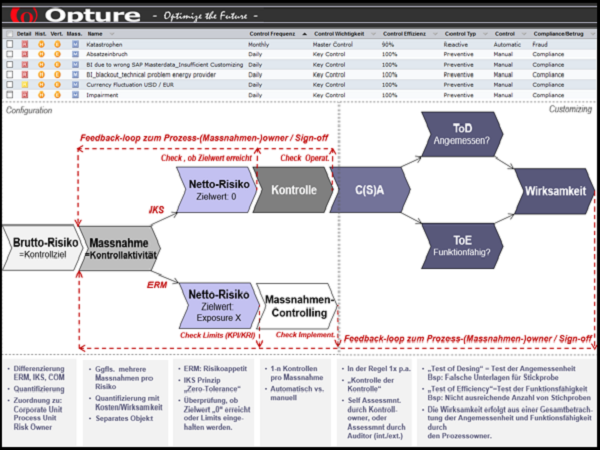
The Opture 5i-Concept characterizes the unique selling proposition of the Opture risk management software:
Intuitive usability and "look & feel" for a high user acceptance.
Innovative methods and functionalities for the hierarchical aggregation of risk data and ensuring highest data quality.
Intelligent filter functions for efficient risk analysis and optimal risk steering.
Individual configuration and administration of the software for mapping customer-specific structures and individual authorization rights.
Informative reporting through automatically updated and event- or addressee-related risk reports.
Risk Management Software from Opture
The Opture Risk Management Software is modularely upgradeable from a simple ERM (=Enterprisewide Risk Management) software Opture ERM Basic for beginners, over the Opture ERM Advanced version with Monte Carlo simulation for experienced risk managers up to the Opture ERM Expert version for professionals. All software solutions from Opture are intuitive to use, customer configurable, individually administrable, easy to implement and available in multiple languages.